Phishing and How to Identify It

Author: Ivan Shyshkou
Phishing is a type of internet fraud when an attacker tries to steal confidential user data in any available way. Phishing is the easiest cyberattack method. However, it is one of the most dangerous and effective cyberattacks. By providing various examples of phishing emails, we will explain how to identify and avoid phishing scams.
What danger does phishing pose?
Phishing attacks are especially dangerous because they target a person and it is impossible to be fully protected from these attacks. Evidently, it is advisable and necessary to conduct regular workshops or other training programs in companies to increase the level of the employees’ awareness in the field of information security.
Phishing techniques have been constantly changing and growing in sophistication. If a user ‘takes the bait’ and follows a phishing link, then he or she is directed to a website that imitates a legitimate internet resource. On this website, the user are asked to log in using their account name and password. As soon as they do that, their data fall into the hands of the attackers, who then use these data to steal confidential information.
Mailing lists are mainly used for the following two purposes:
- Without arousing suspicion, steal confidential information from a person using the body of a letter and input fields (for example, on a phishing site or in a program that simulates internal corporate software)
- Trick the user to download a file (from a letter, a website, a torrent) and do something with it (for example, launch an application, open a document in Word, enable macros), also without arousing suspicion. Eventually, the downloaded malicious file can exploit vulnerabilities in the user’s system and simply steal data
How to identify phishing?
There are several signs that can help you understand that you are dealing with a phishing email, website or message:
- Domain. While phishing, the domain name of the site where users have to enter their data is very much alike the original one. But if you study it carefully, you can spot the differences. For example, using the letter ‘l’ instead of the letter ‘I’ in the domain will be practically indistinguishable. An inexperienced user may not notice the substitution and attackers are counting on this.
- Contents of the letter. As a rule, both the subject of the letter and its contents are composed in such a way so as to exert psychological pressure on the recipient. They provoke the victim to follow the phishing link without delay and with no questions asked in order to pay a fine, extend a domain, collect winnings, delete compromising materials, etc.
- Appearance of the letter. If the letter contains a lot of grammatical errors or an outdated company logo, then it is highly possible that it is phishing. It is also worth paying attention to how the sender of the letter addresses the recipient. If the greeting begins with an impersonal address, for example, Dear friend, or the recipient’s email address is indicated, then most likely the letter is phishing and attackers use mass mailing.
Examples of phishing emails
Fake invoice scam
Let’s start with arguably the most popular phishing template out there – the fake invoice technique. Like many phishing attacks, this scam relies on fear and urgency, pressuring an end user to submit a payment for goods or services they have never even ordered or received.
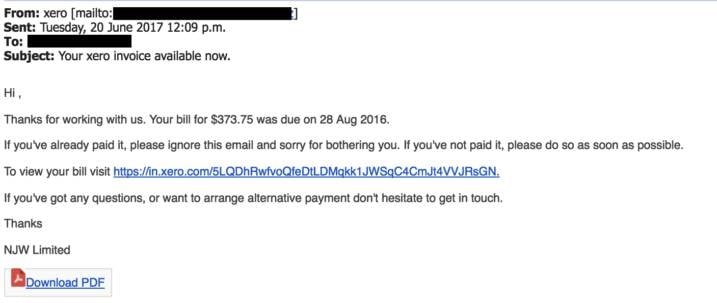
Fake invoice scam
Finance departments are the obvious targets for this sort of attacks, although there are plenty of potential victims to be duped.
Unusual activity scam
When receiving an email or text stating that there has been “suspicious activity on your account”, alarm bells start ringing at full pace. That is why this scam works so well for scammers, as victims do not just face urgency and panic, but also confusion.
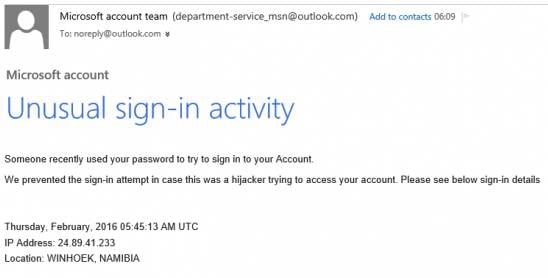
Unusual activity scam
This is just one example of where an unusual activity scam can come from. Any app, website or platform – whether it be your bank or even your Instagram account – can be used by an attacker for this damaging technique.
Nowadays, hackers and ordinary scammers resort to sophisticated methods of social engineering. For example, to make a letter look more authentic, hackers can pretend to be employees of your company. To get fewer questions about the letter’s contents, attackers can send letters dealing with the technical component of a product to non-technical specialists, thereby inducing them to open the letter and take the necessary steps.
Let’s look at more examples of phishing emails.
A letter is sent to non-technical employees on behalf of IT employees. It deals with testing of a new remote access scheme and suggests clicking on the phishing link to check the availability of the service by entering your credentials. The phishing portal’s appearance, design, and the text are tailored to fit the corporate style.
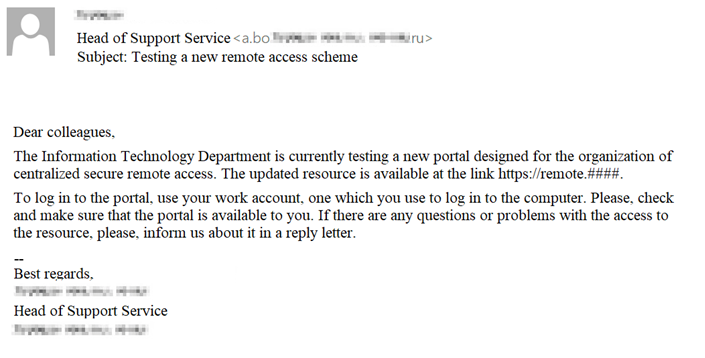
Phishing email for the first script
And technical specialists are sent letters dealing with HR specialists’ paperwork, encouraging them to go through the steps indicated in the letter. For example, arranging vacations or medical insurance.
The following scenario is provided for technical support specialists of different levels. They received a letter from an HR manager on the possibility of obtaining a voluntary health insurance. A .docx file with an alleged insurance program was attached to the letter.
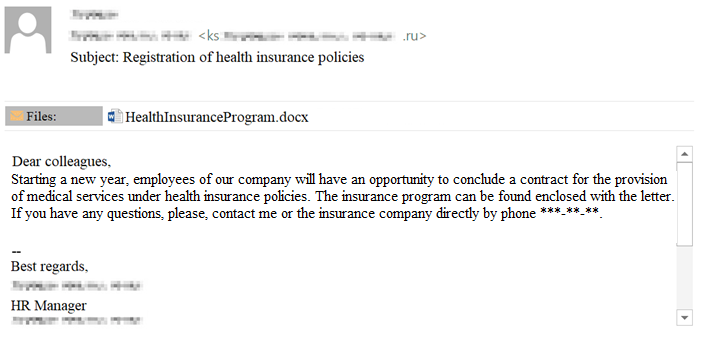
Phishing email for the second script
The opened file looked empty. It was to provoke the recipient to “Allow editing” in the hope of finding the text. At that moment, the account under which the document was opened is automatically authenticated. On the side of our server, the domain account name and the NTLMv2 hash of the password are fixed.
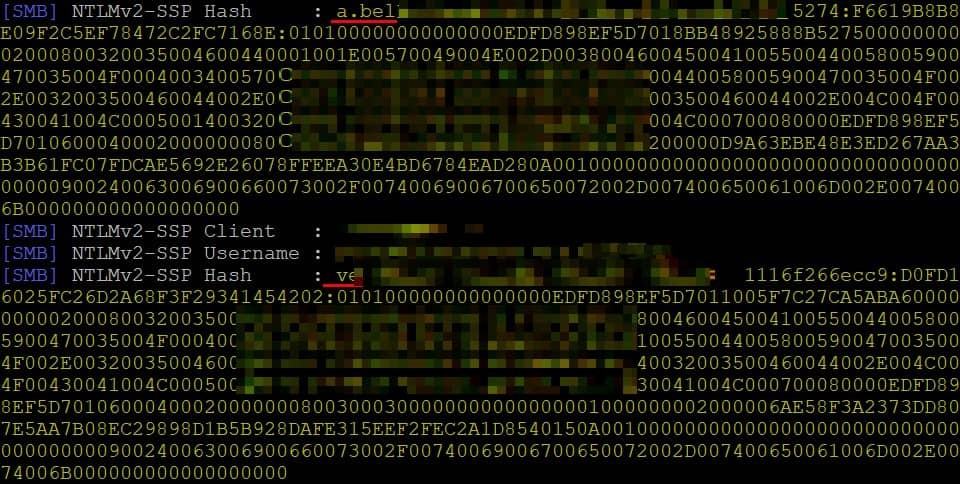
Intercepted hash from domain accounts
Conclusion
Phishing has remained one of the most common types of attacks so far, as hacking a user rather than a computer is much easier. A popular saying goes that the most vulnerable component of any information system is located between a computer chair and a keyboard. A person can be absent-minded, inattentive, or insufficiently informed, thus becoming the target of phishing attacks, and the consequences of the latter are sometimes really detrimental.
The conclusion is obvious. The reliability of the weak link in question must be checked no less carefully than software or hardware configuration. And we at IBA Group offer penetration testing services with additional training of personnel in how to resist social engineering and phishing attacks.
This is the third part of our cybersecurity series that I prepared in cooperation with my team, namely Artyom Litvin, and Ivan Shyshkou.
Stay tuned to discover more about cyber security and read the first and second part about it here.